Table of Contents
XRouter Tour - Telnet Interfaces
Up to 3 types of “telnet” interface can be configured on XRouter.
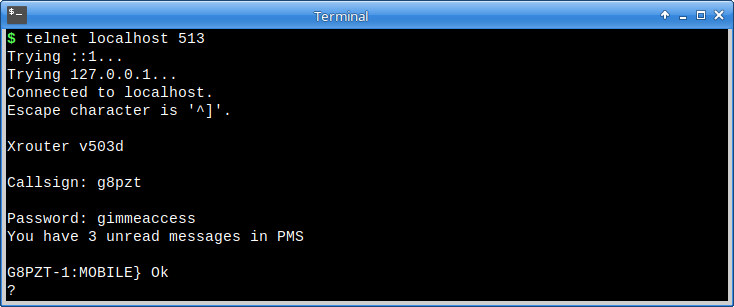
The general purpose one defaults to TCP port 23. There's a sysop-only one, usually on TCP port 513, and one for machine-to-machine interactions, the so-called “Telnet Proxy”. These are described below:
Standard Telnet
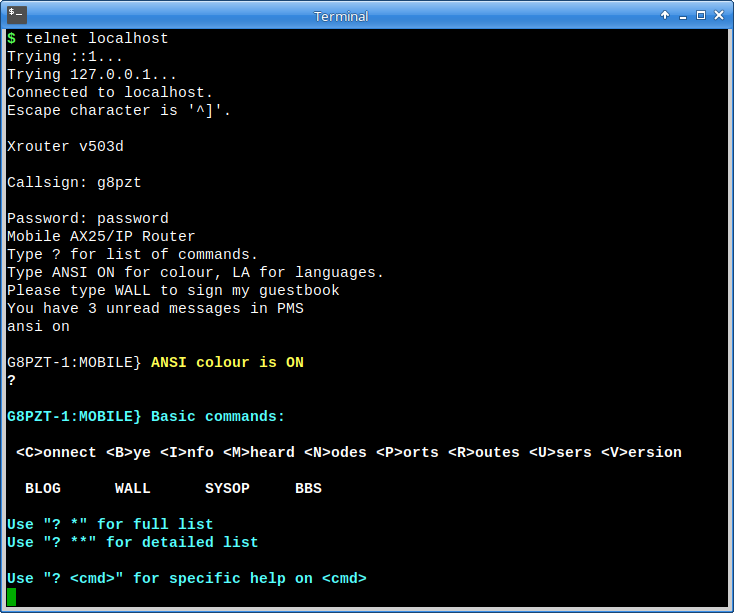
Here's a typical login to port 23 from a Linux terminal:
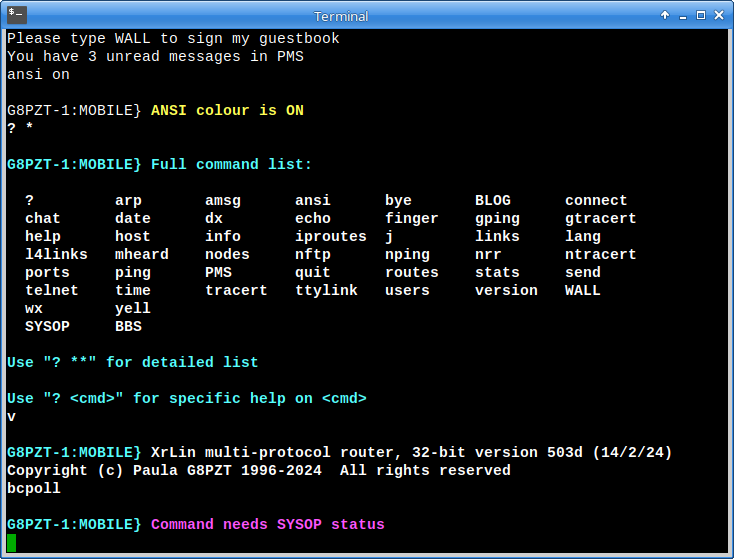
If you so desire, the “normal” telnet interface can be opened to the wider world, because connections to that port do NOT have “sysop” privileges, as can be seen by the reduced command set in the following example:
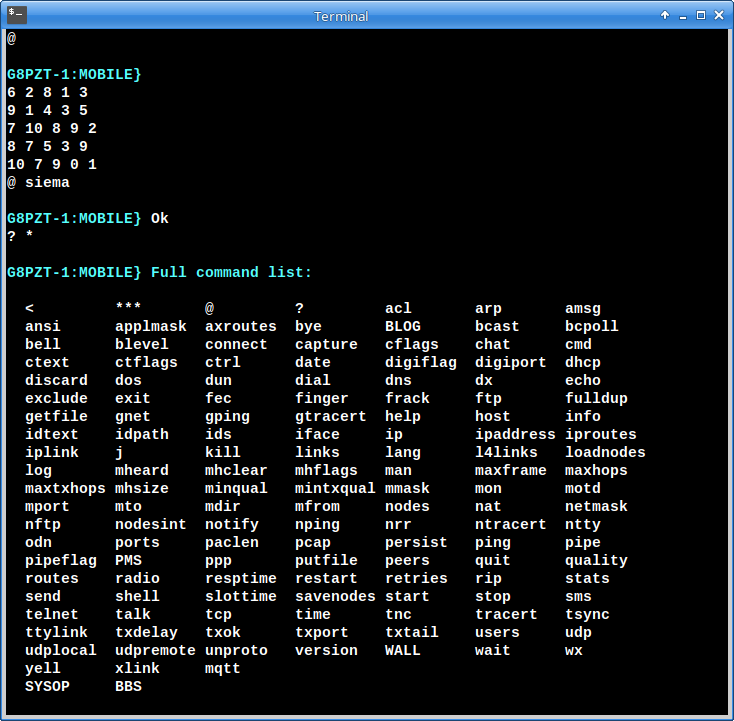
You can gain sysop privileges using the “@” command in one of two ways. The following example shows how you might do it via an insecure link such as IP over radio. Entering “@” by itself produces a “password grid”. The caller picks one line from the grid and sends the corresponding characters from their password:
(Note the larger command set available to sysops)
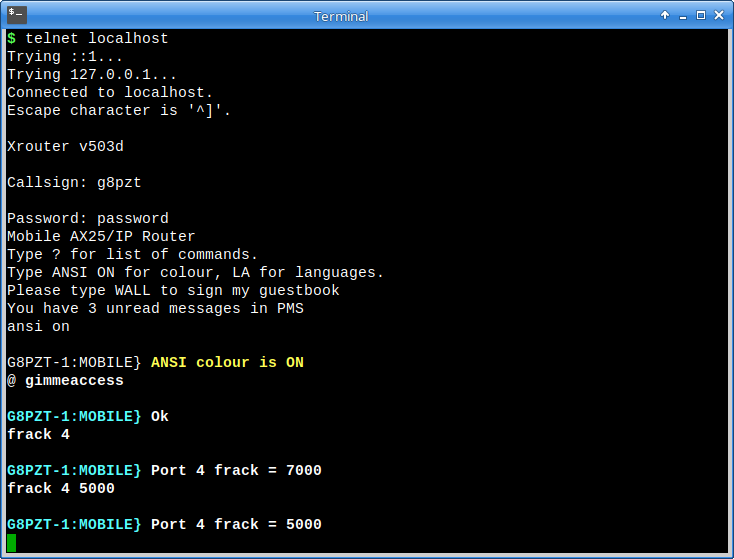
The other way to gain sysop privileges, on a more secure uplink, would be to issue the @ command followed by the plain text password, for example:
Remote Login (RLOGIN)
RLOGINPORT, if enabled, is intended for sysops-only. You can connect directly as a sysop, using your “sysop” password instead of your “user” one…
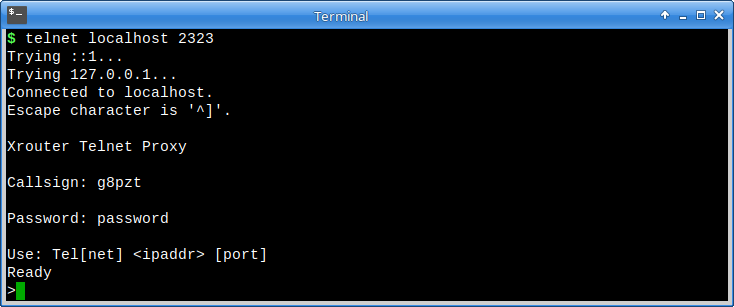
Telnet Proxy
The telnet proxy is intended mainly for machine-to-machine operations, e.g. to allow a TCP application to control the node or make outgoing NetRom/AX25 connections. The difference between this and “normal” telnet is that, after the password challenge is completed, the session switches to pure binary mode.
The telnet proxy has been used by a several applications, including a BBS and a node crawler.
(The text sent after login is configurable).
On the next page we'll look at a typical use of the telnet proxy.